Download Bitlocker Windows 8
How To Enable BitLocker Drive Encryption In Windows 10? Although the way BitLocker works is pretty complicated, enabling it to secure your data in Windows 10 is a walk in the park. The whole process is really simple, easy and takes a few clicks. User Guide: How to Turn On BitLocker in Windows 10 Home Edition with Hasleo BitLocker Anywhere? Download and install Hasleo BitLocker Anywhere. In Windows Explorer, right-click the drive letter you want to encrypt, then click 'BitLocker Anywhere' > 'Turn On BitLocker'.
- Please press the key combination [Win-Logo]+[R], then simply type the command control.exe /name Microsoft.BitLockerDriveEncryption, or start the BitLocker via.Windows-8 Control Panel. In the BitLocker-Drive-Encryption select the drive to be encrypted.
- Hi, I realize that you are trying to enable Bit Locker in your system. I like to inform you that; bit locker is build in feature of Windows operating system, you no need to download any additional application to enabler bit locker in your system /drives.
Applies to
- Windows 10
This topic provides a high-level overview of BitLocker, including a list of system requirements, practical applications, and deprecated features.
BitLocker overview
BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
BitLocker provides the most protection when used with a Trusted Platform Module (TPM) version 1.2 or later. The TPM is a hardware component installed in many newer computers by the computer manufacturers. It works with BitLocker to help protect user data and to ensure that a computer has not been tampered with while the system was offline.
On computers that do not have a TPM version 1.2 or later, you can still use BitLocker to encrypt the Windows operating system drive. However, this implementation will require the user to insert a USB startup key to start the computer or resume from hibernation. Starting with Windows 8, you can use an operating system volume password to protect the operating system volume on a computer without TPM. Both options do not provide the pre-startup system integrity verification offered by BitLocker with a TPM.
In addition to the TPM, BitLocker offers the option to lock the normal startup process until the user supplies a personal identification number (PIN) or inserts a removable device, such as a USB flash drive, that contains a startup key. These additional security measures provide multifactor authentication and assurance that the computer will not start or resume from hibernation until the correct PIN or startup key is presented.
Practical applications
Data on a lost or stolen computer is vulnerable to unauthorized access, either by running a software-attack tool against it or by transferring the computer's hard disk to a different computer. BitLocker helps mitigate unauthorized data access by enhancing file and system protections. BitLocker also helps render data inaccessible when BitLocker-protected computers are decommissioned or recycled.
There are two additional tools in the Remote Server Administration Tools, which you can use to manage BitLocker.
BitLocker Recovery Password Viewer. The BitLocker Recovery Password Viewer enables you to locate and view BitLocker Drive Encryption recovery passwords that have been backed up to Active Directory Domain Services (AD DS). You can use this tool to help recover data that is stored on a drive that has been encrypted by using BitLocker. The BitLocker Recovery Password Viewer tool is an extension for the Active Directory Users and Computers Microsoft Management Console (MMC) snap-in.By using this tool, you can examine a computer object's Properties dialog box to view the corresponding BitLocker recovery passwords. Additionally, you can right-click a domain container and then search for a BitLocker recovery password across all the domains in the Active Directory forest. To view recovery passwords, you must be a domain administrator, or you must have been delegated permissions by a domain administrator.
BitLocker Drive Encryption Tools. BitLocker Drive Encryption Tools include the command-line tools, manage-bde and repair-bde, and the BitLocker cmdlets for Windows PowerShell. Both manage-bde and the BitLocker cmdlets can be used to perform any task that can be accomplished through theBitLocker control panel, and they are appropriate to use for automated deployments and other scripting scenarios. Repair-bde is provided for disaster recovery scenarios in which a BitLocker protected drive cannot be unlocked normally or by using the recovery console.
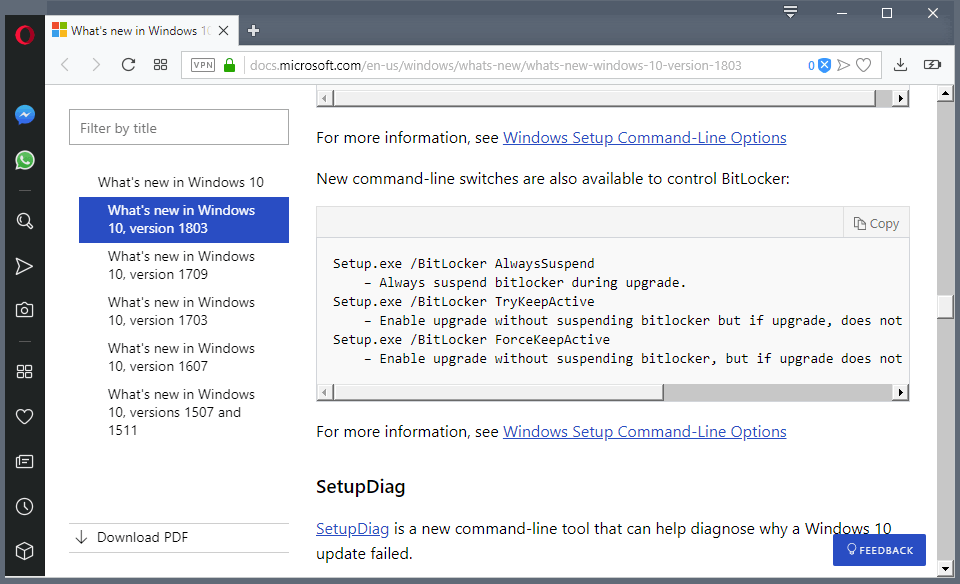
New and changed functionality
To find out what's new in BitLocker for Windows 10, such as support for the XTS-AES encryption algorithm, see the BitLocker section in 'What's new in Windows 10.'

System requirements
BitLocker has the following hardware requirements:
For BitLocker to use the system integrity check provided by a Trusted Platform Module (TPM), the computer must have TPM 1.2 or later. If your computer does not have a TPM, enabling BitLocker requires that you save a startup key on a removable device, such as a USB flash drive.
A computer with a TPM must also have a Trusted Computing Group (TCG)-compliant BIOS or UEFI firmware. The BIOS or UEFI firmware establishes a chain of trust for the pre-operating system startup, and it must include support for TCG-specified Static Root of Trust Measurement. A computer without a TPM does not require TCG-compliant firmware.
The system BIOS or UEFI firmware (for TPM and non-TPM computers) must support the USB mass storage device class, including reading small files on a USB flash drive in the pre-operating system environment.
Note
TPM 2.0 is not supported in Legacy and CSM Modes of the BIOS. Devices with TPM 2.0 must have their BIOS mode configured as Native UEFI only. The Legacy and Compatibility Support Module (CSM) options must be disabled. For added security Enable the Secure Boot feature.
Installed Operating System on hardware in legacy mode will stop the OS from booting when the BIOS mode is changed to UEFI. Use the tool MBR2GPT before changing the BIOS mode which will prepare the OS and the disk to support UEFI.
The hard disk must be partitioned with at least two drives:
- The operating system drive (or boot drive) contains the operating system and its support files. It must be formatted with the NTFS file system.
- The system drive contains the files that are needed to load Windows after the firmware has prepared the system hardware. BitLocker is not enabled on this drive. For BitLocker to work, the system drive must not be encrypted, must differ from the operating system drive, and must be formatted with the FAT32 file system on computers that use UEFI-based firmware or with the NTFS file system on computers that use BIOS firmware. We recommend that system drive be approximately 350 MB in size. After BitLocker is turned on it should have approximately 250 MB of free space.
When installed on a new computer, Windows will automatically create the partitions that are required for BitLocker.
When installing the BitLocker optional component on a server you will also need to install the Enhanced Storage feature, which is used to support hardware encrypted drives.
In this section
| Topic | Description |
|---|---|
| Overview of BitLocker Device Encryption in Windows 10 | This topic for the IT professional provides an overview of the ways that BitLocker Device Encryption can help protect data on devices running Windows 10. |
| BitLocker frequently asked questions (FAQ) | This topic for the IT professional answers frequently asked questions concerning the requirements to use, upgrade, deploy and administer, and key management policies for BitLocker. |
| Prepare your organization for BitLocker: Planning and policies | This topic for the IT professional explains how can you plan your BitLocker deployment. |
| BitLocker basic deployment | This topic for the IT professional explains how BitLocker features can be used to protect your data through drive encryption. |
| BitLocker: How to deploy on Windows Server | This topic for the IT professional explains how to deploy BitLocker on Windows Server. |
| BitLocker: How to enable Network Unlock | This topic for the IT professional describes how BitLocker Network Unlock works and how to configure it. |
| BitLocker: Use BitLocker Drive Encryption Tools to manage BitLocker | This topic for the IT professional describes how to use tools to manage BitLocker. |
| BitLocker: Use BitLocker Recovery Password Viewer | This topic for the IT professional describes how to use the BitLocker Recovery Password Viewer. |
| BitLocker Group Policy settings | This topic for IT professionals describes the function, location, and effect of each Group Policy setting that is used to manage BitLocker. |
| BCD settings and BitLocker | This topic for IT professionals describes the BCD settings that are used by BitLocker. |
| BitLocker Recovery Guide | This topic for IT professionals describes how to recover BitLocker keys from AD DS. |
| Protect BitLocker from pre-boot attacks | This detailed guide will help you understand the circumstances under which the use of pre-boot authentication is recommended for devices running Windows 10, Windows 8.1, Windows 8, or Windows 7; and when it can be safely omitted from a device’s configuration. |
| Protecting cluster shared volumes and storage area networks with BitLocker | This topic for IT pros describes how to protect CSVs and SANs with BitLocker. |
| Enabling Secure Boot and BitLocker Device Encryption on Windows 10 IoT Core | This topic covers how to use BitLocker with Windows 10 IoT Core |
BitLocker is a tool built into Windows that lets you encrypt an entire hard drive for enhanced security. Here’s how to set it up.
When TrueCrypt controversially closed up shop, they recommended their users transition away from TrueCrypt to using BitLocker or Veracrypt. BitLocker has been around in Windows long enough to be considered mature, and is an encryption product generally well-regarded by security pros. In this article, we’re going to talk about how you can set it up on your PC.
RELATED:Should You Upgrade to the Professional Edition of Windows 10?
Note: BitLocker Drive Encryption and BitLocker To Go require a Professional or Enterprise edition of Windows 8 or 10, or the Ultimate version of Windows 7. However, starting with Windows 8.1, the Home and Pro editions of Windows include a “Device Encryption” feature (a feature also included in Windows 10) that works similarly. We recommend Device Encryption if your computer supports it, BitLocker for Pro users who can’t use Device Encryption, and VeraCrypt for people using a Home version of Windows where Device Encryption won’t work.
Encrypt an Entire Drive or Create an Encrypted Container?
Many guides out there talk about creating a BitLocker container that works much like the kind of encrypted container you can create with products like TrueCrypt or Veracrypt. It’s a bit of a misnomer, but you can achieve a similar effect. BitLocker works by encrypting entire drives. That could be your system drive, a different physical drive, or a virtual hard drive (VHD) that exists as a file and is mounted in Windows.
RELATED:How to Create an Encrypted Container File With BitLocker on Windows
The difference is largely semantic. In other encryption products, you usually create an encrypted container, and then mount it as a drive in Windows when you need to use it. With BitLocker, you create a virtual hard drive, and then encrypt it. If you’d like to use a container rather than, say, encrypt your existing system or storage drive, check out our guide to creating an encrypted container file with BitLocker.
For this article, we’re going to concentrate on enabling BitLocker for an existing physical drive.
How to Encrypt a Drive with BitLocker
RELATED:How to Use BitLocker Without a Trusted Platform Module (TPM)
To use BitLocker for a drive, all you really have to do is enable it, choose an unlock method—password, PIN, and so on—and then set a few other options. Before we get into that, however, you should know that using BitLocker’s full-disk encryption on a system drive generally requires a computer with a Trusted Platform Module (TPM) on your PC’s motherboard. This chip generates and store the encryption keys that BitLocker uses. If your PC doesn’t have a TPM, you can use Group Policy to enable using BitLocker without a TPM. It’s a bit less secure, but still more secure than not using encryption at all.
You can encrypt a non-system drive or removable drive without TPM and without having to enable the Group Policy setting.
On that note, you should also know that there are two types of BitLocker drive encryption you can enable:
- BitLocker Drive Encryption: Sometimes referred to just as BitLocker, this is a “full-disk encryption” feature that encrypts an entire drive. When your PC boots, the Windows boot loader loads from the System Reserved partition, and the boot loader prompts you for your unlock method—for example, a password. BitLocker then decrypts the drive and loads Windows. The encryption is otherwise transparent—your files appear like they normally would on an unencrypted system, but they’re stored on the disk in an encrypted form. You can also encrypt other drives than just the system drive.
- BitLocker To Go: You can encrypt external drives—such as USB flash drives and external hard drives—with BitLocker To Go. You’ll be prompted for your unlock method—for example, a password—when you connect the drive to your computer. If someone doesn’t have the unlock method, they can’t access the files on the drive.
In Windows 7 through 10, you really don’t have to worry about making the selection yourself. Windows handles things behind the scenes, and the interface you’ll use to enable BitLocker doesn’t look any different. If you end up unlocking an encrypted drive on Windows XP or Vista, you’ll see the BitLocker to Go branding, so we figured you should at least know about it.
So, with that out of the way, let’s go over how this actually works.
Step One: Enable BitLocker for a Drive
The easiest way to enable BitLocker for a drive is to right-click the drive in a File Explorer window, and then choose the “Turn on BitLocker” command. If you don’t see this option on your context menu, then you likely don’t have a Pro or Enterprise edition of Windows and you’ll need to seek another encryption solution.
It’s just that simple. The wizard that pops up walks you through selecting several options, which we’ve broken down into the sections that follow.
Step Two: Choose an Unlock Method
The first screen you’ll see in the “BitLocker Drive Encryption” wizard lets you choose how to unlock your drive. You can select several different ways of unlocking the drive.
If you’re encrypting your system drive on a computer that doesn’t have a TPM, you can unlock the drive with a password or a USB drive that functions as a key. Select your unlock method and follow the instructions for that method (enter a password or plug in your USB drive).
RELATED:How to Enable a Pre-Boot BitLocker PIN on Windows
If your computer does have a TPM, you’ll see additional options for unlocking your system drive. For example, you can configure automatic unlocking at startup (where your computer grabs the encryption keys from the TPM and automatically decrypts the drive). You could also use a PIN instead of a password, or even choose biometric options like a fingerprint.
If you’re encrypting a non-system drive or removable drive, you’ll see only two options (whether you have a TPM or not). You can unlock the drive with a password or a smart card (or both).
Step Three: Back Up Your Recovery Key
BitLocker provides you with a recovery key that you can use to access your encrypted files should you ever lose your main key—for example, if you forget your password or if the PC with TPM dies and you have to access the drive from another system.
You can save the key to your Microsoft account, a USB drive, a file, or even print it. These options are the same whether you’re encrypting a system or non-system drive.
If you back up the recovery key to your Microsoft account, you can access the key later at https://onedrive.live.com/recoverykey. If you use another recovery method, be sure to keep this key safe—if someone gains access to it, they could decrypt your drive and bypass encryption.
You can also back up your recovery key multiple ways if you want. Just click each option you want to use in turn, and then follow the directions. When you’re done saving your recovery keys, click “Next” to move on.
Note: If you’re encrypting a USB or other removable drive, you won’t have the option of saving your recovery key to a USB drive. You can use any of the other three options.
Step Four: Encrypt and Unlock the Drive
BitLocker automatically encrypts new files as you add them, but you must choose what happens with the files currently on your drive. You can encrypt the entire drive—including the free space—or just encrypt the used disk files to speed up the process. These options are also the same whether you’re encrypting a system or non-system drive.
RELATED:How to Recover a Deleted File: The Ultimate Guide
Download limewire 4.18.8 free: free download – FrostWire 5.3.6: Open source alternative to LimeWire, and much more programs. Old Version of Limewire 4.18.8 Download – OldApps.com LimeWire is a free and open source Gnutella peer-to-peer network client released under the GNU General Public License. Limewire free 4.18.8 free downloads, limewire 4.18.8 pro, pub golf score card 18 hole, bitmaps 18 x 18 - software for free at freeware freedownload. LimeWire 4.18.8 Change Log. OldVersion Blog. OldVersion.com Launches Android Apps Section Posted on Jul 25, 2016 12:45 AM. OldVersion.com provides free software downloads for old versions of programs, drivers and games. So why not downgrade to the version you love? Because newer is not always better! Free LimeWire Download, LimeWire 4.18.8 Download. LimeWire is a Internet software developed by Lime Wire LLC. After our trial and test, the software is proved to be official, secure and free. /limewire-418-8-free-download.html.
If you’re setting up BitLocker on a new PC, encrypt the used disk space only—it’s much faster. If you’re setting BitLocker up on a PC you’ve been using for a while, you should encrypt the entire drive to ensure no one can recover deleted files.
When you’ve made your selection, click the “Next” button.
Step Five: Choose an Encryption Mode (Windows 10 Only)
If you’re using Windows 10, you’ll see an additional screen letting you choose an encryption method. If you’re using Windows 7 or 8, skip ahead to the next step.
Windows 10 introduced a new encryption method named XTS-AES. It provides enhanced integrity and performance over the AES used in Windows 7 and 8. If you know the drive you’re encrypting is only going to be used on Windows 10 PCs, go ahead and choose the “New encryption mode” option. If you think you might need to use the drive with an older version of Windows at some point (especially important if it’s a removable drive), choose the “Compatible mode” option.
Whichever option you choose (and again, these are the same for system and non-system drives), go ahead and click the “Next” button when you’re done, and on the next screen, click the “Start Encrypting” button.
Step Six: Finishing Up
The encryption process can take anywhere from seconds to minutes or even longer, depending on the size of the drive, the amount of data you’re encrypting, and whether you chose to encrypt free space.
If you’re encrypting your system drive, you’ll be prompted to run a BitLocker system check and restart your system. Make sure the option is selected, click the “Continue” button, and then restart your PC when asked. After the PC boots back up for the first time, Windows encrypts the drive.
If you’re encrypting a non-system or removable drive, Windows does not need to restart and encryption begins immediately.
Whatever type of drive you’re encrypting, you can check the BitLocker Drive Encryption icon in the system tray to see its progress, and you can continue using your computer while drives are being encrypted—it will just perform more slowly.
Unlocking Your Drive
If your system drive is encrypted, unlocking it depends on the method you chose (and whether your PC has a TPM). If you do have a TPM and elected to have the drive unlocked automatically, you won’t notice anything different—you’ll just boot straight into Windows like always. If you chose another unlock method, Windows prompts you to unlock the drive (by typing your password, connecting your USB drive, or whatever).
RELATED:How to Recover Your Files From a BitLocker-Encrypted Drive
And if you’ve lost (or forgotten) your unlock method, press Escape on the prompt screen to enter your recovery key.
If you’ve encrypted a non-system or removable drive, Windows prompts you to unlock the drive when you first access it after starting Windows (or when you connect it to your PC if it’s a removable drive). Type your password or insert your smart card, and the drive should unlock so you can use it.
• First person persepective, turn based battle system with visual representation of just the monsters and not players. • Character sets now by default are square-sized such as those found in classic/retro JRPGs. • Supports audio file formats of MIDI, OGG, MP3 and WAV. Rpg maker vx free download. • Limited number of tilesets may be used throughout your whole game, and each map may only be mapped with two layers.
Download Bit Locker For Windows 8
In File Explorer, encrypted drives show a gold lock on the icon (on the left). That lock changes to gray and appears unlocked when you unlock the drive (on the right).
You can manage a locked drive—change the password, turn off BitLocker, back up your recovery key, or perform other actions—from the BitLocker control panel window. Right-click any encrypted drive, and then select “Manage BitLocker” to go directly to that page.
Like all encryption, BitLocker does add some overhead. Microsoft’s official BitLocker FAQ says that “Generally it imposes a single-digit percentage performance overhead.” If encryption is important to you because you have sensitive data—for example, a laptop full of business documents—the enhanced security is well worth the performance trade-off.
Can't Find Bitlocker Windows 10
READ NEXTDownload Bitlocker Windows 10 64 Bit Home
- › Six Common Smarthome Mistakes Beginners Make
- › What Can I Do with My Old iPhone?
- › Free Download: Microsoft’s PowerToys for Windows 10
- › How to Overclock Your Computer’s RAM
- › What’s New in Chrome 77, Arriving September 10